Active Directory Lab 2 – VMWare
Project Overview
This project demonstrates the implementation of a Windows Server 2022 Active Directory environment using VMware Workstation Pro, focusing on organizational unit structure, user management, and Group Policy implementation in an enterprise-like configuration. We use a Windows 10 admin PC with RSAT downloaded to remotely configure Active Directory.

Domain controller installation and configuration were explained in our first AD lab, so we will not get into those details here. Note: We typically download RSAT tools on our admin, remote PC and manage AD through there. This is done using the Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call (RPC) protocols.
- LDAP is what enables you to access as well as manage directory services over the network. It is conceptually similar to REST APIs (more on that in a future project). RPC is what makes it seem that you are locally on the server.
Organizational Unit Design
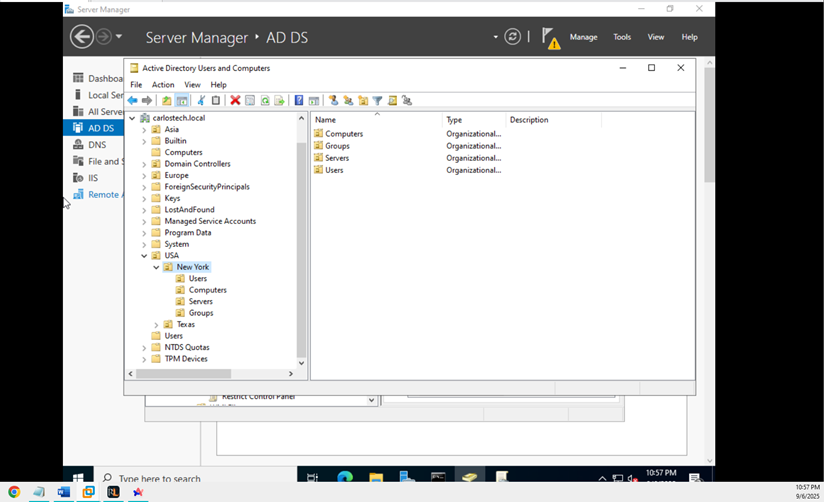
We designed an organizational structure that simulates an enterprise that spans globally. Using geographic-based OUs allows for location-specific Group Policy applications, delegated administration by region and a scalable design for future expansion. Here, we’re just going to configure the USA folder – and we are going to create sub-OUs with the states of where our offices are located. In these state OUs, we’re going to have our users, computers, servers, and groups.
- Note: In production environments, state-level OUs would typically include additional subdivisions such as offices, cities, or more specific business units for advanced granular management.
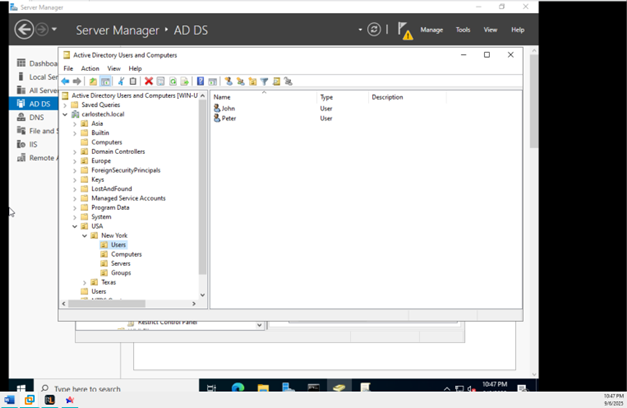
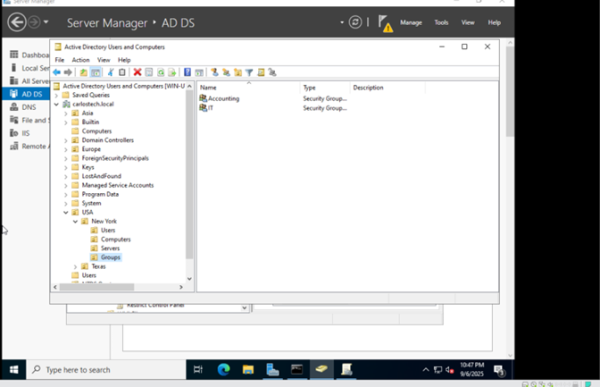
- If I added Peter to the ‘IT’ security group, he would have all the privileges/permissions of that group and whatever permissions he already had assigned to him. If I created a GPO for the “Users” OU, but I did NOT want Peter to receive it, I can use the ‘GPO Security Filtering’ option to not allow the GPO to apply to the group “IT”. This is an example of how in-depth GPOs and AD administration can be.
- The OU structure can be nested to any depth that you require, which enables precise administrative segmentation based on whichever requirements you have.
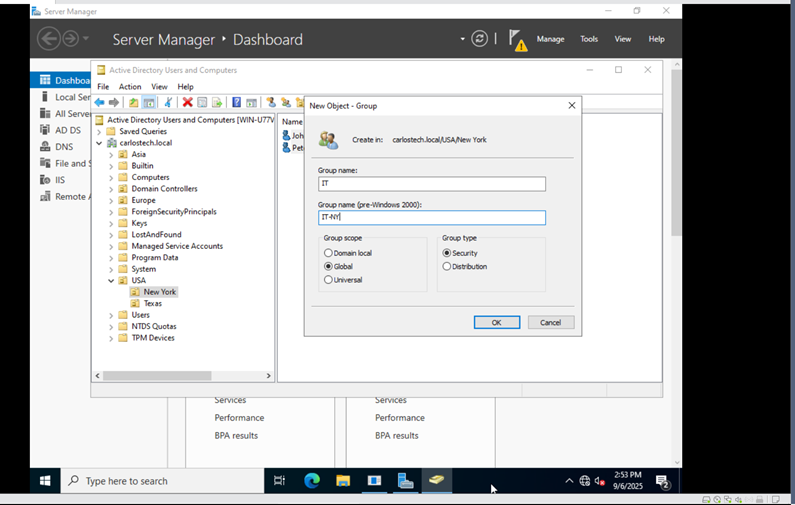
Note: Security groups provide authorization and access control, while distribution groups serve exclusively for email distribution. This distinction is crucial for proper access management in enterprise environments.
Group Policy Implementation
In Group Policy Management we begin creating different Group Policy Objects (GPOs). We created some for Account Lockout policies, Password Policies, restricting access to the Control Panel, and even disabling the use of USB devices.
- Note: There are two main ways to apply GPOs here. Either apply them to the computer themselves or the users. For password policies, we always want to apply it to the computer because we want everyone to have a secure password, so the computer will always force you to create a secure password. For control panel access, we should configure it on a user basis. We don’t want to completely lock out the control panel because what if an IT admin needs access to it? We just want to prevent users that shouldn’t have the authority from reaching it.
- To put it simple: Configure computer configuration policies based on: “It doesn’t matter who logs into this computer, this computer should behave in this manner always” – by blocking USB storage use and enforcing password policies, the pc will always be hardened and secure.
- For user configurations, the key is: No matter which computer they log onto, this specific user should always have these settings/permissions.
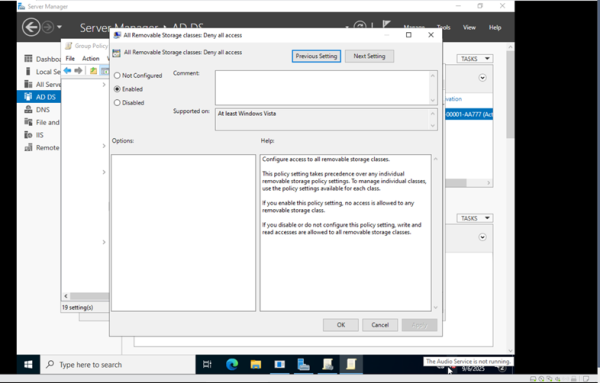
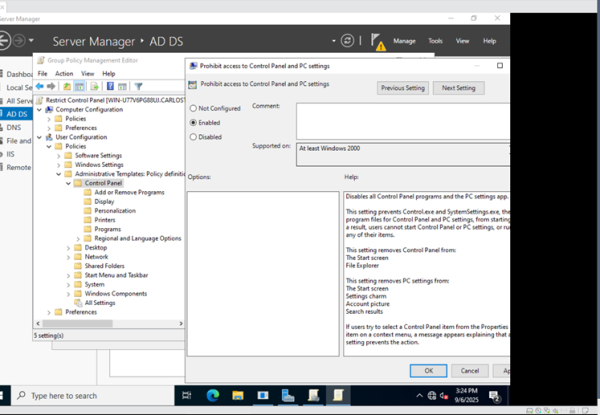
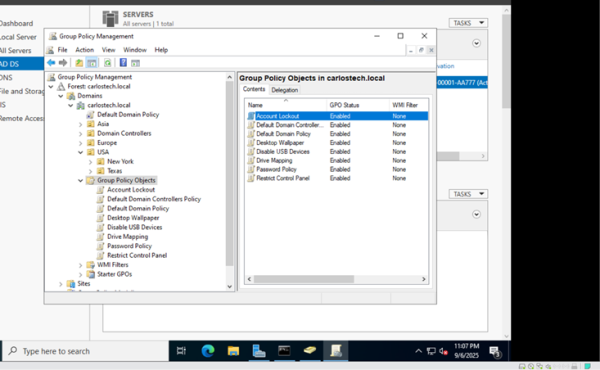
If you create the GPOs directly on the domain name, all OUs under it inherit the GPOs. This also applies for OUs nested under parent OUs if you link GPOs to the parent instead.
These GPOs will also automatically appear in the “Group Policy Objects folder” (this folder stores ALL GPOs no matter where you initially created them). By creating the GPOs in GPO folder, you don’t link them anywhere just yet – they’re just created.
- Before we link GPOs to wherever we deem necessary, let’s go back to our Windows 10 Enterprise machine and join it to our domain – so we can test if GPOs applied. We do this in settings on our PC.

Note: VMWare creates virtual networks and provides a virtual DHCP/DNS server; the 192.168.x.x network you see. Whenever a VM host needs to reach the actual Internet, it goes through your host computer (because this is a Type 2 Hypervisor).

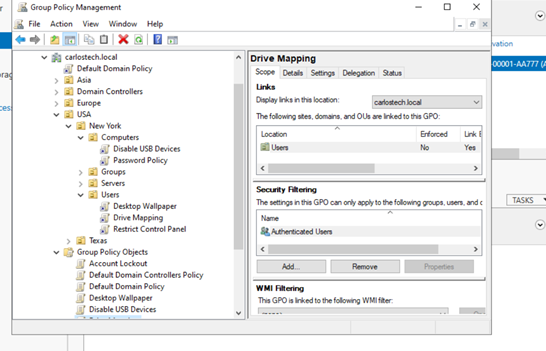
We’re then going to link our GPOs to the correct OUs. Our Computers OU, containing our Windows 10 Enterprise machine, is going to have linked the USB and Password Policy GPOs. The Users OU will receive the Control Panel, Drive Mapping (more on that in another project) and Wallpaper policies.
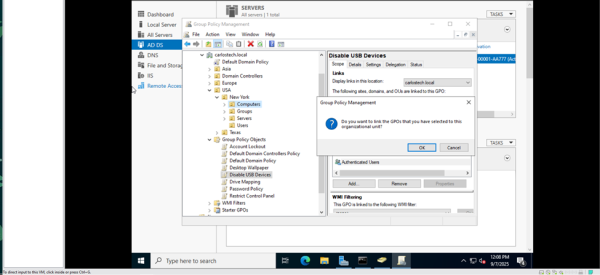
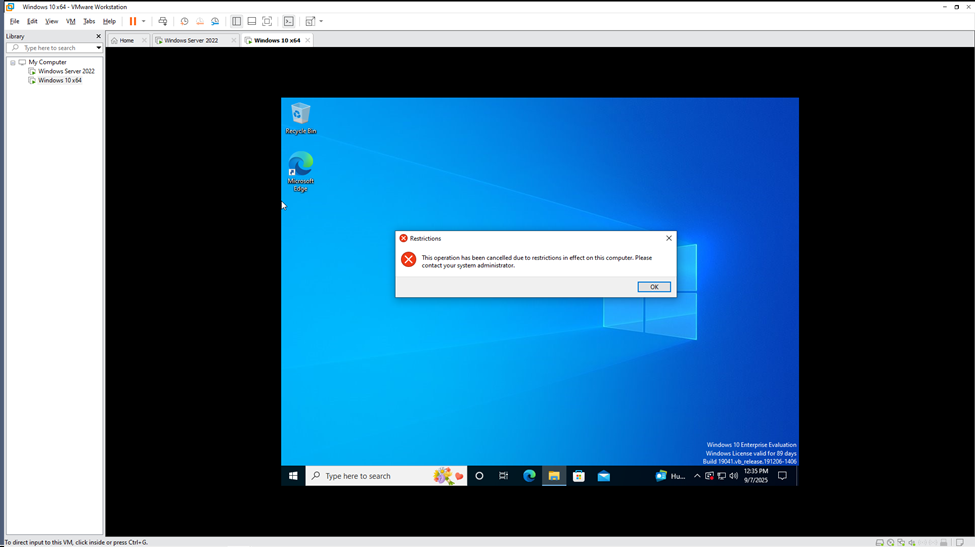
Now, let’s test these GPOs. The one that would be easiest to check right now is the user’s access to the Control Panel.

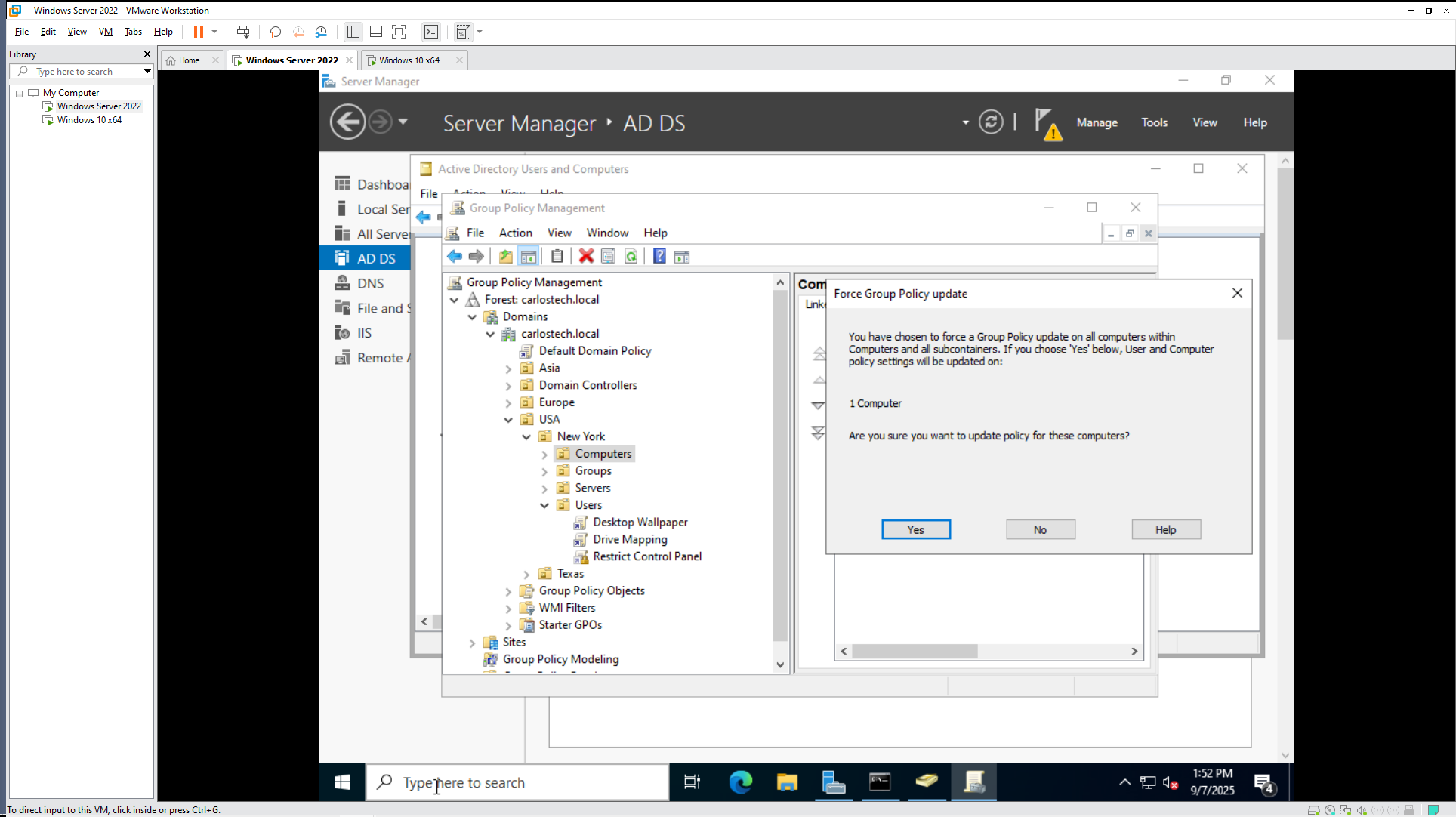
As you can see, in Peter’s workstation I’m still able to access the control panel. The reason this happens is because Group Policy updates over a period – not instantly, which is typically 90-120 minutes with a random offset of up to 30 minutes (this is to prevent network congestion – you do not want hundreds or even thousands of machines contacting the AD server at the same time to refresh their policies).
Therefore, we need to force this update onto the machine. There are various methods to do this:
- PowerShell command (target machines must have Windows Remote Management, PowerShell remoting enabled and there cannot be firewall rules preventing remote connections).
- In the GPMC GUI
- On the PC’s cmd line using “gpupdate /force”

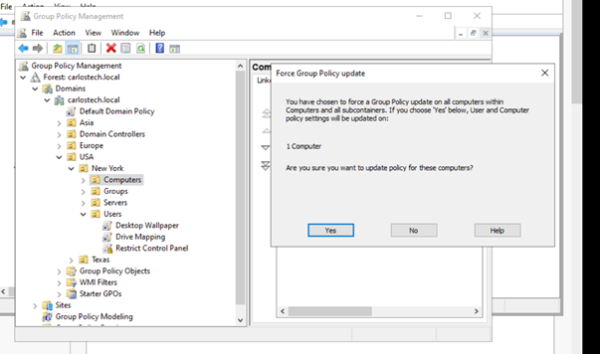
An important distinction here is that I wanted to apply the GPO on the user ‘Peter’ but didn’t force the GPO update on the ‘Users’ OU. Instead, I forced it on the ‘Computers’ OU which contained the machine that the user Peter was signed into. As you can see, it states that it would apply computer AND user policies when I click yes. The GPMC needs a target machine to apply the GPOs.
This only applies to the user who is CURRENTLY logged on (only that signed in user’s policies will be immediately forced at that moment). If Peter signs in at a later time and even on a different machine, the update will still be applied because user policies are applied at logon.
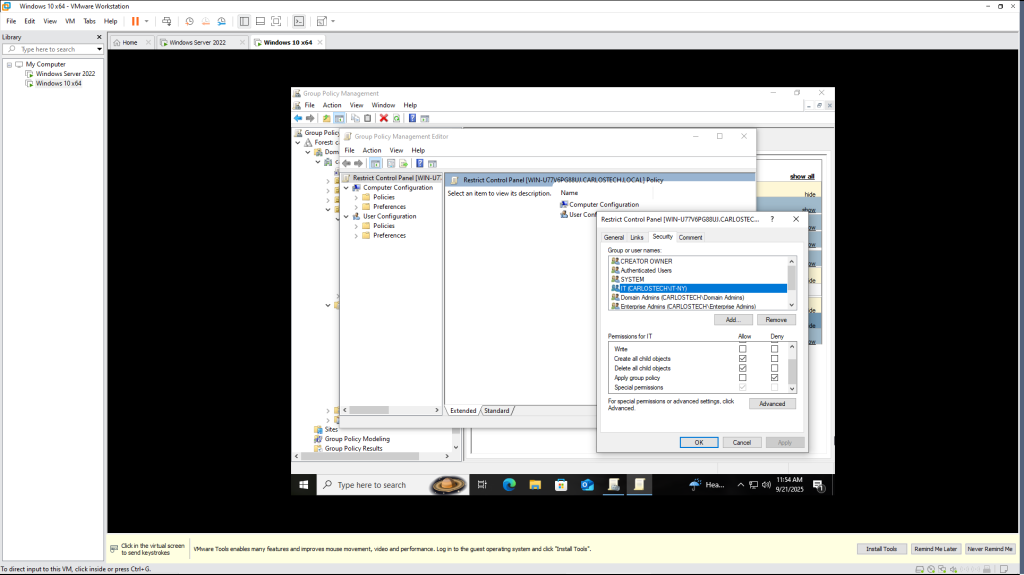
Let’s take it a step further and apply the security filter we discussed earlier.
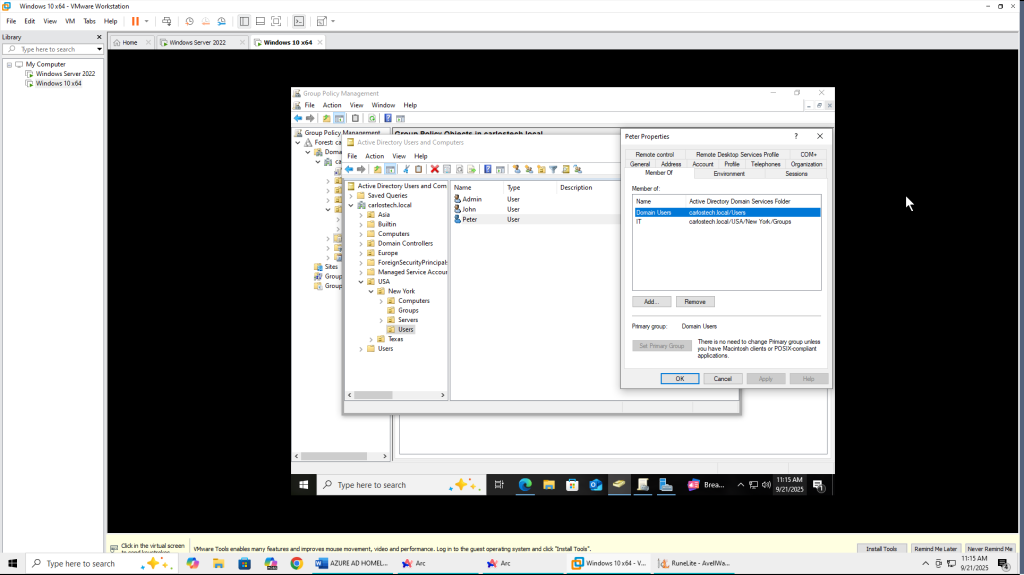
- Peter is officially a member of the “IT” security group.
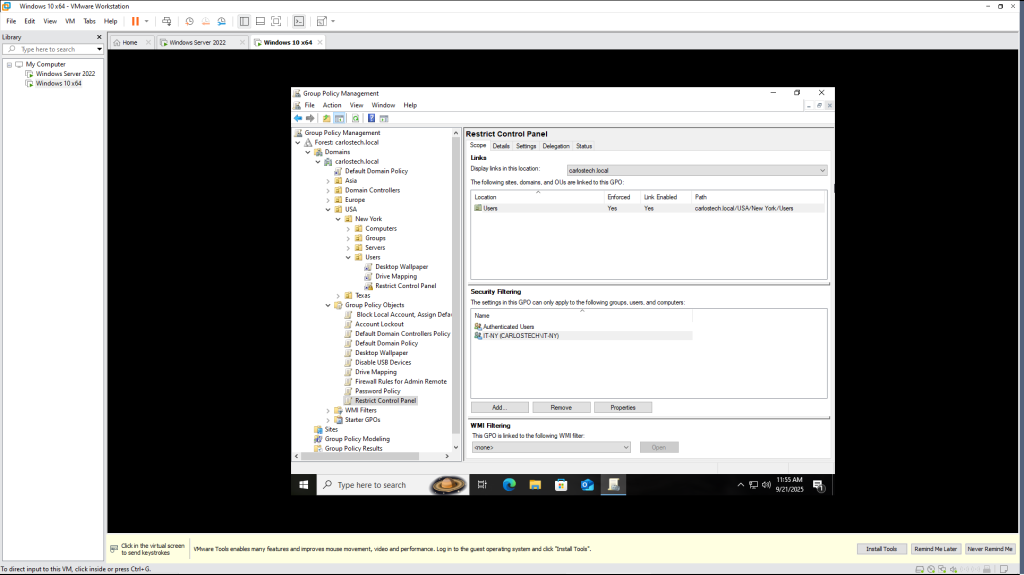
- Here, I added the security group “IT” in the security filtering for the GPO that disables Control Panel access so this GPO “applies” to this group.
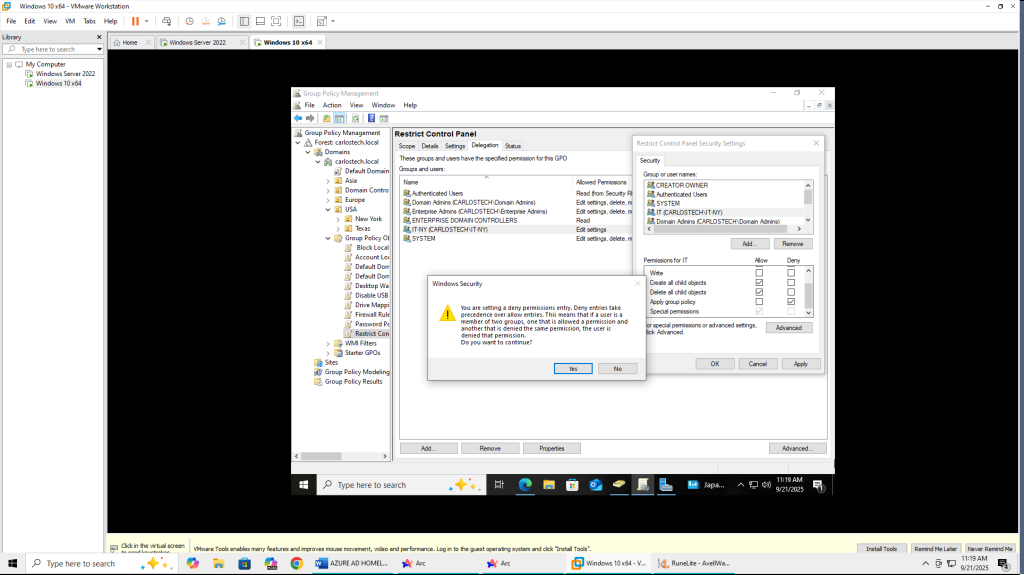
In the delegation tab, in permissions for IT, I clicked “deny” for the option to apply this group policy to this group. So, members of the IT security group should still have access to the Control Panel, even though these members, like Peter, would be under the OU “Users” that this GPO is applied to.
- Deny permissions have greater priority over allow.
One thing I discovered is that GPMC could sometimes contain a bug where you apply this permission and it appears it was not “saved”. To confirm if the GPO was applied, you right click the GPO and click “Edit”. In that new menu, you right click the name of the GPO and click Properties. Under Security, you’ll see that the GPO was indeed applied.
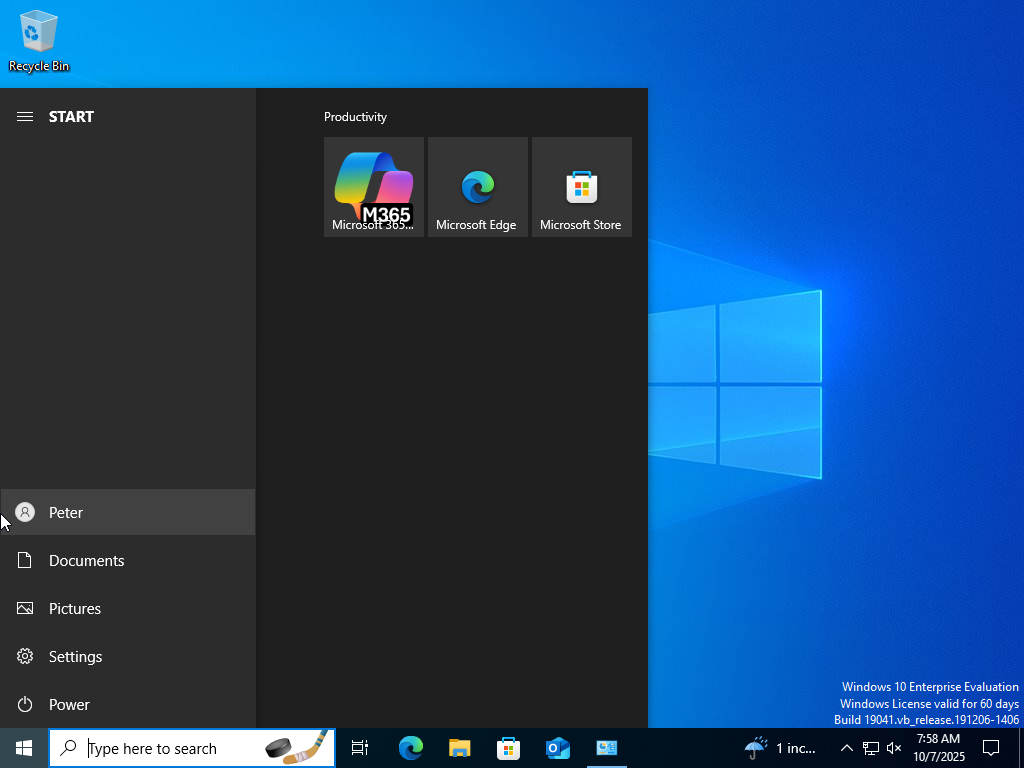
- Now we log onto the user Peter and check if he has access to the Control Panel. Recall earlier in the project that he was denied access because the GPO was applied.
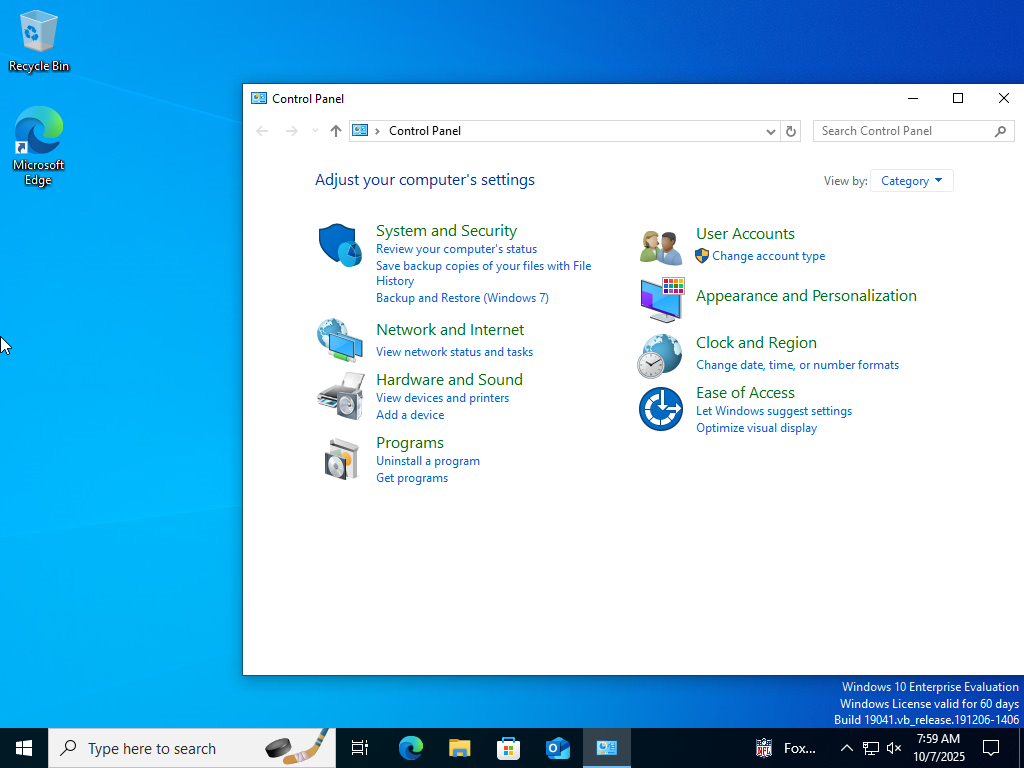
Through the use of security filtering, since Peter was a member of the “IT” security group, and this group was “denied” application of this GPO to its group, Peter now has access to the Control Panel once again.
Note: It is EXTREMELY important that all machines within the same domain have the same time as their AD server. Explicitly, you must sync the time on the PC with the AD server itself. This should theoretically happen automatically when you join a machine into the domain but nothing is ever guaranteed. Both machines were using the EST time zone, however the Windows 10 Enterprise machine was off about 10 minutes; and as a result, I received errors in how the machine didn’t trust the action being performed because the AD server time was different (this has to do with Kerberos).
- This shows how crucial Network Time Protocol (NTP) can be.
Another issue that arose during this lab was that my Windows 10 Enterprise machine was easily able to ping the AD server, but the AD server was unable to ping the Windows 10 machine.
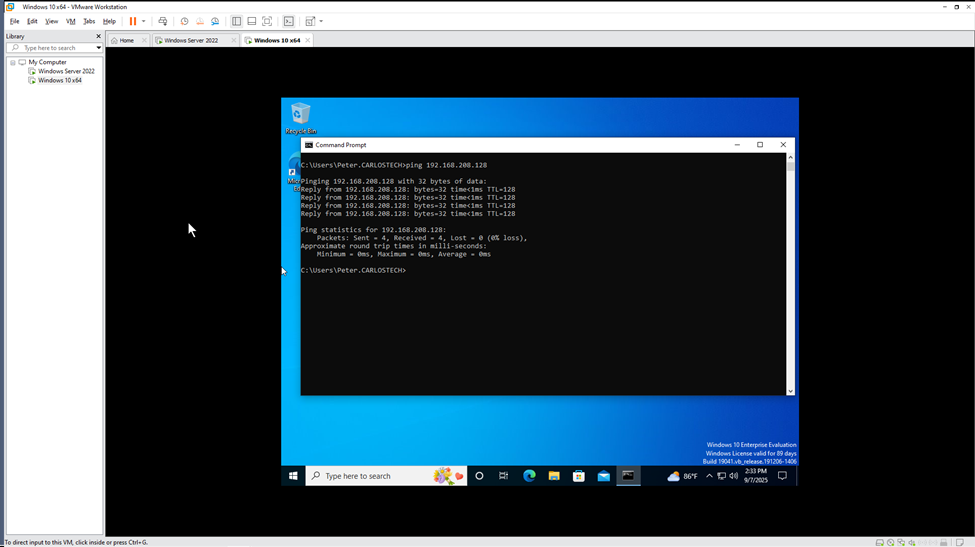
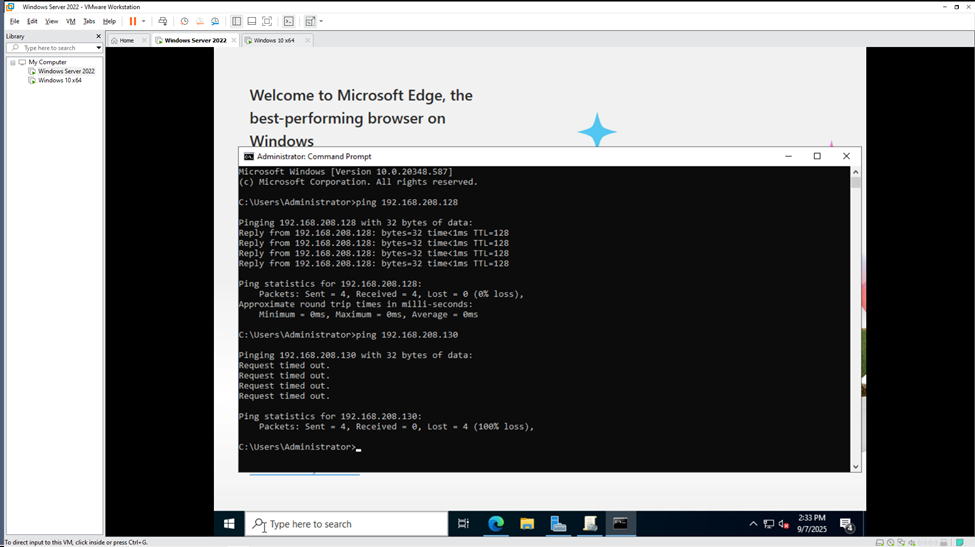
I discovered this issue when I tried to force the GPO update through the GPMC GUI. What this meant: the network was working fine – both machines were in the same subnet with the same default gateway. One machine was able to communicate perfectly with the other. When the other couldn’t, the most likely scenario was: a firewall was blocking incoming traffic.
- I couldn’t look at the firewall because I applied the command line “gpupdate /force” command which disabled access to the Control Panel. After some research, the solution was to enable and turn on “network discovery and file/printer sharing” which is automatically off when you provision a VMWare Virtual Machine. This resulted in the Windows firewall now enabling inbound traffic for Internet Control Message Protocol (ICMP – what you use to ping), RPC (port 135) and Server Message Block (port 445 – this is important because PCs download policy files using SMB), exactly what I needed to force a gpupdate through the GPMC GUI.
To finish off this project the last thing I will do is create one last GPO: disable the use of the local account “Peter” we created when the VM was first established (this is NOT the same as the domain user Peter that we configured earlier). This is a security benefit as it reduces attack surface by eliminating local admin accounts that can bypass certain security policies.
- The first thing we are doing is creating a GPO that assigns a default domain to logon into – that way all users don’t have to manually enter the domain every single time or do a form of “peter@carlostech.local” to log on.
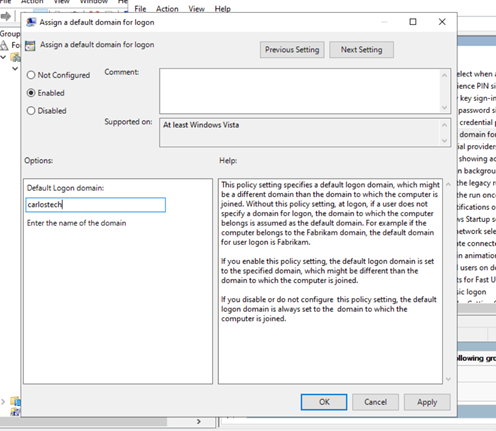
- You can use carlostech or carlostech.local. The first option is NETBIOs (fundamentally the same as ARP but maps names to IP addresses instead of IP to MAC addresses) and the second option is using DNS. There really isn’t a right or wrong answer here but the DNS option is more specific, so in enterprises that could have multiple domains under a forest, this option would probably be best. Here we used the NETBIOs name for simplicity.
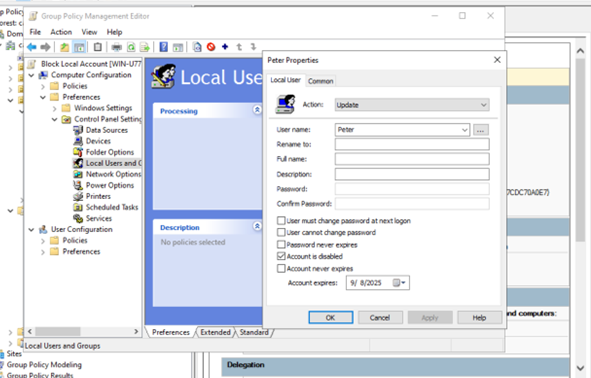
- Then through computer configuration –> Preferences –> Local Users: disabled the local account, Peter.
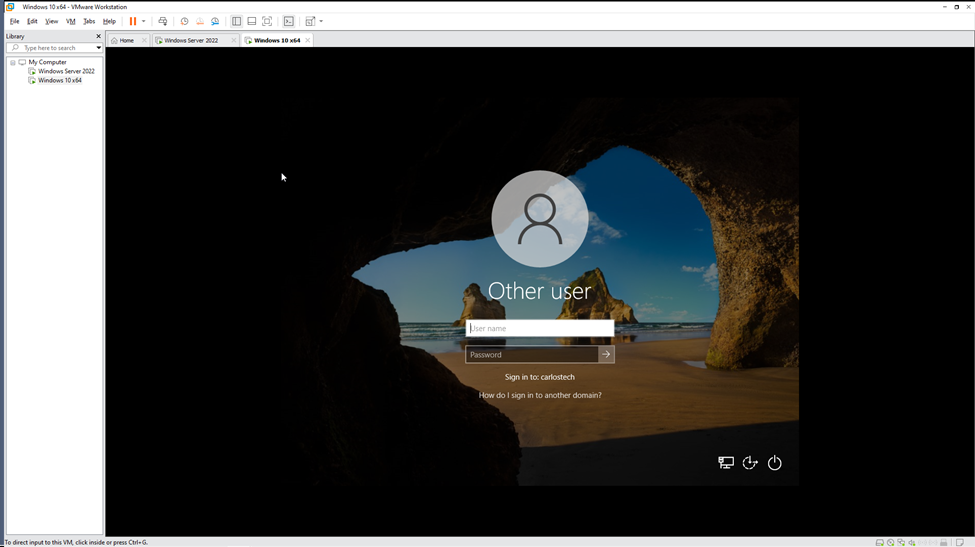
- When attempting to log on to the machine, it now always directs us to log on with a user from the carlostech domain! I am also completely unable to log on with the local account Peter.